Network Exploit Update 2022.11.1
We've just released Nabuware Network Exploit 2022.11.1. This update includes new tools for host and network reconnaissance.
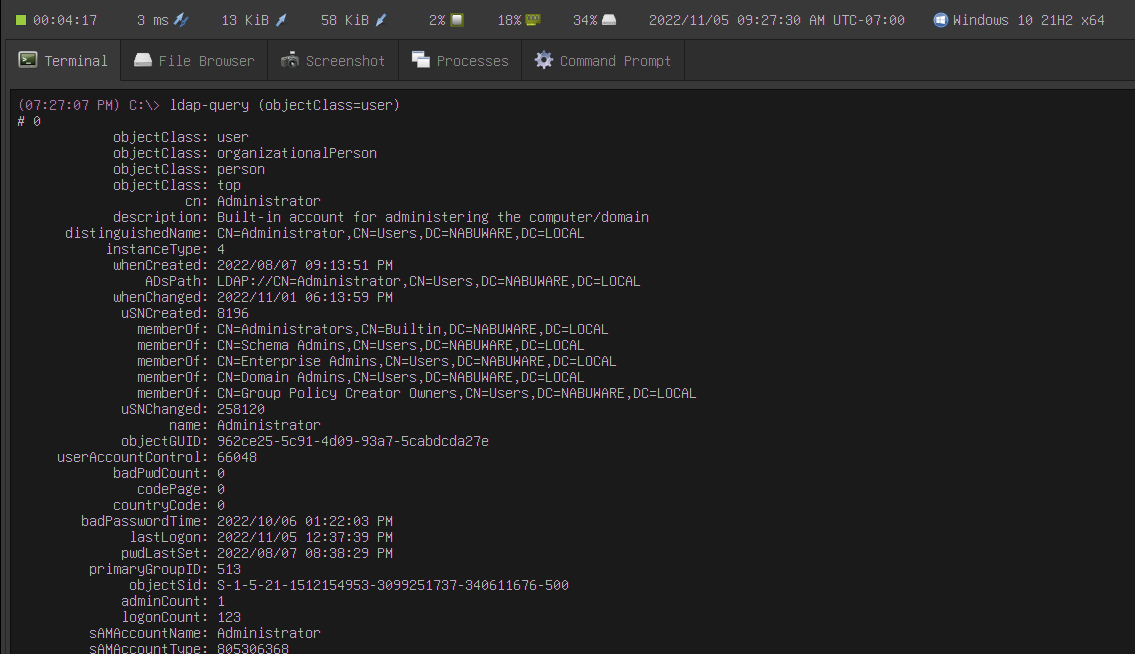
In this update, we added the tool ldap-query, a built-in LDAP client for gathering information in Windows domain networks. You can collect helpful information about high-value network resources such as users, groups, servers, and more. And all you need is a standard domain user.
ldap-query accepts a search filter. LDAP filters are a standard way to search LDAP servers, and there are plenty of resources about this topic online. There exist some other options to specify an LDAP server and user credentials. However, ldap-query will infer these options for you.
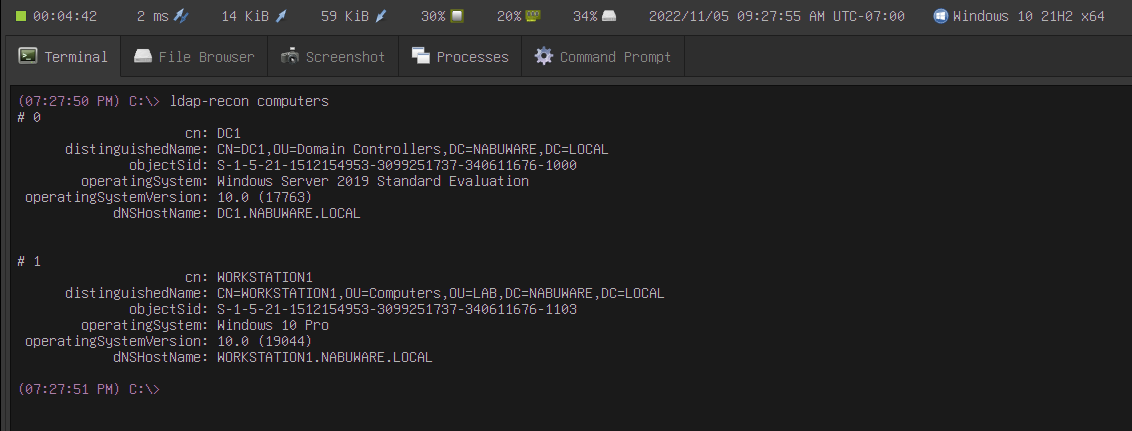
We also added the tool ldap-recon, which offers a set of common pre-built LDAP queries, so you don't have to write these filters yourself:
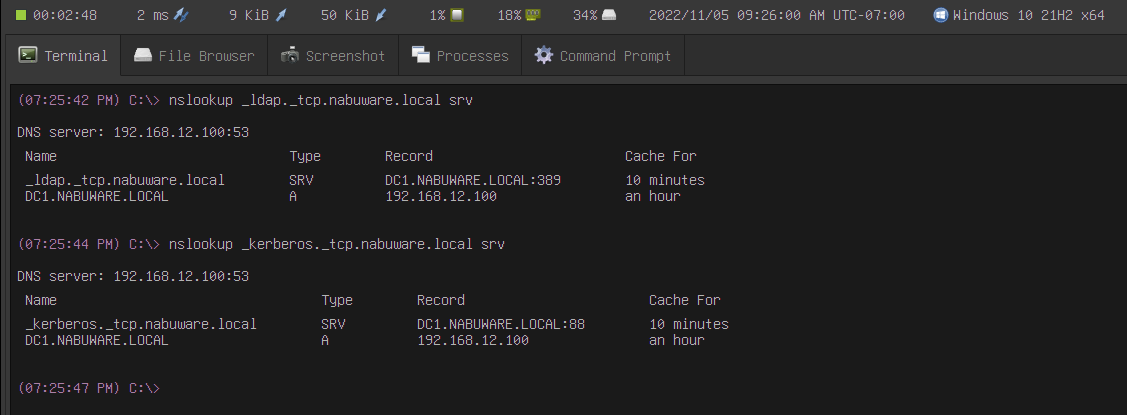
We also updated the nslookup tool to support DNS SRV records. SRV records are a DNS mechanism for locating network services. In the screenshot, you can see an example of using nslookup to find Active Directory LDAP and the Kerberos servers:
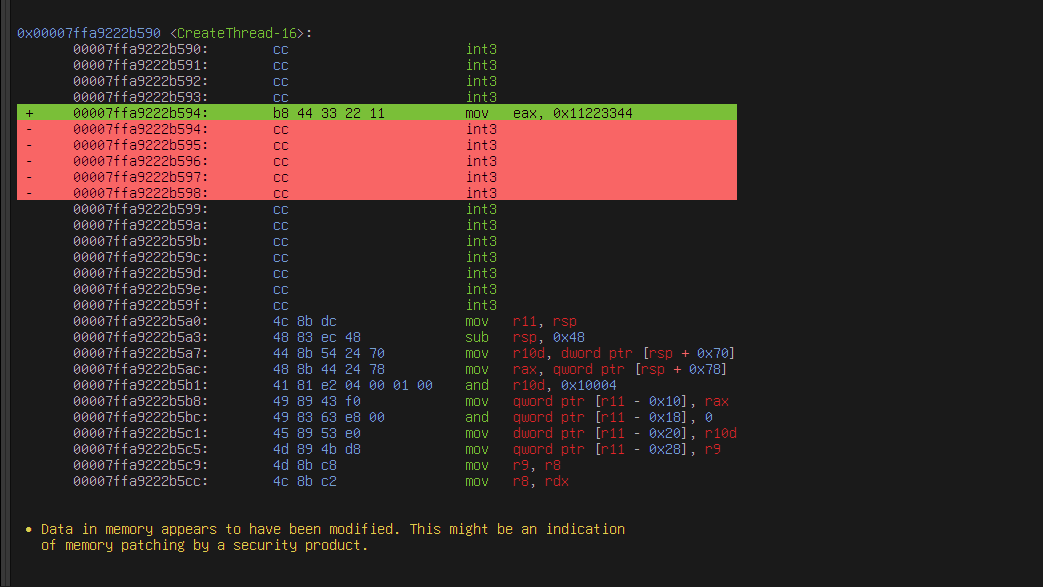
Another tool we added is ps-disasm. This tool is a memory analysis tool that allows you to dissemble memory on the target remotely. Suppose the target uses a security product that does inline hooking. You can collect information about how it works in the context of the target environment without acquiring and installing the product.
Besides its basic functionality, ps-disasm automatically detects memory modifications and anomalies, such as improper memory permissions.
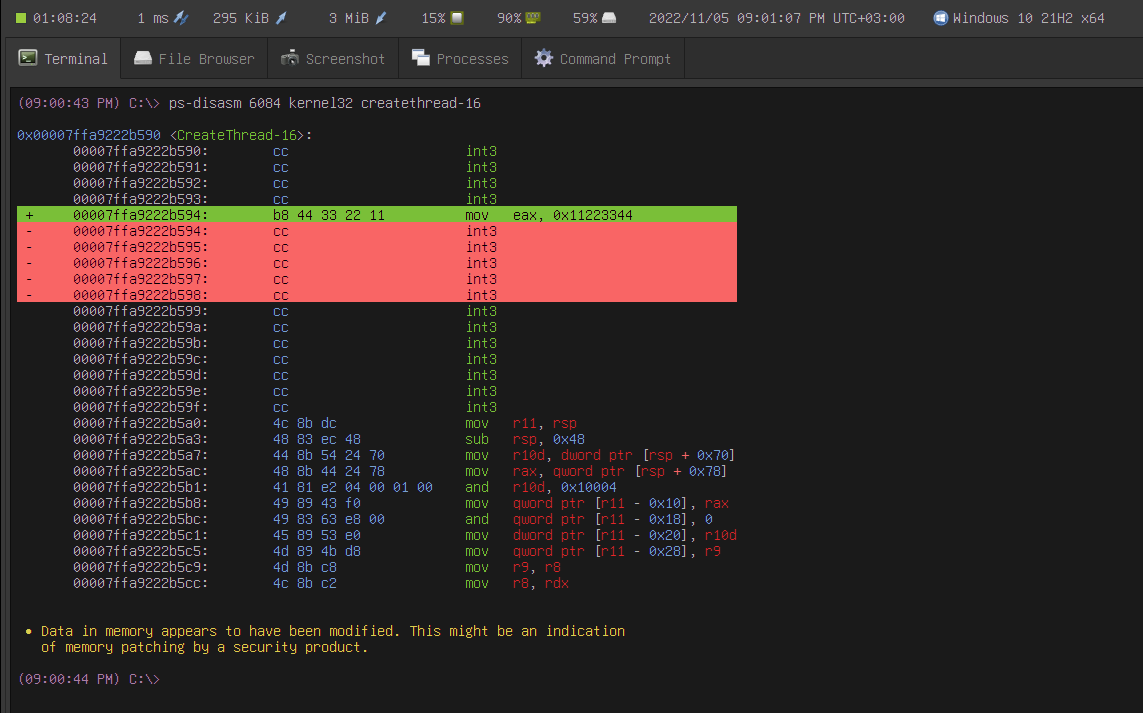
In the previous screenshot, ps-disasm highlighted the added instructions in green and the original overwritten instructions in red.
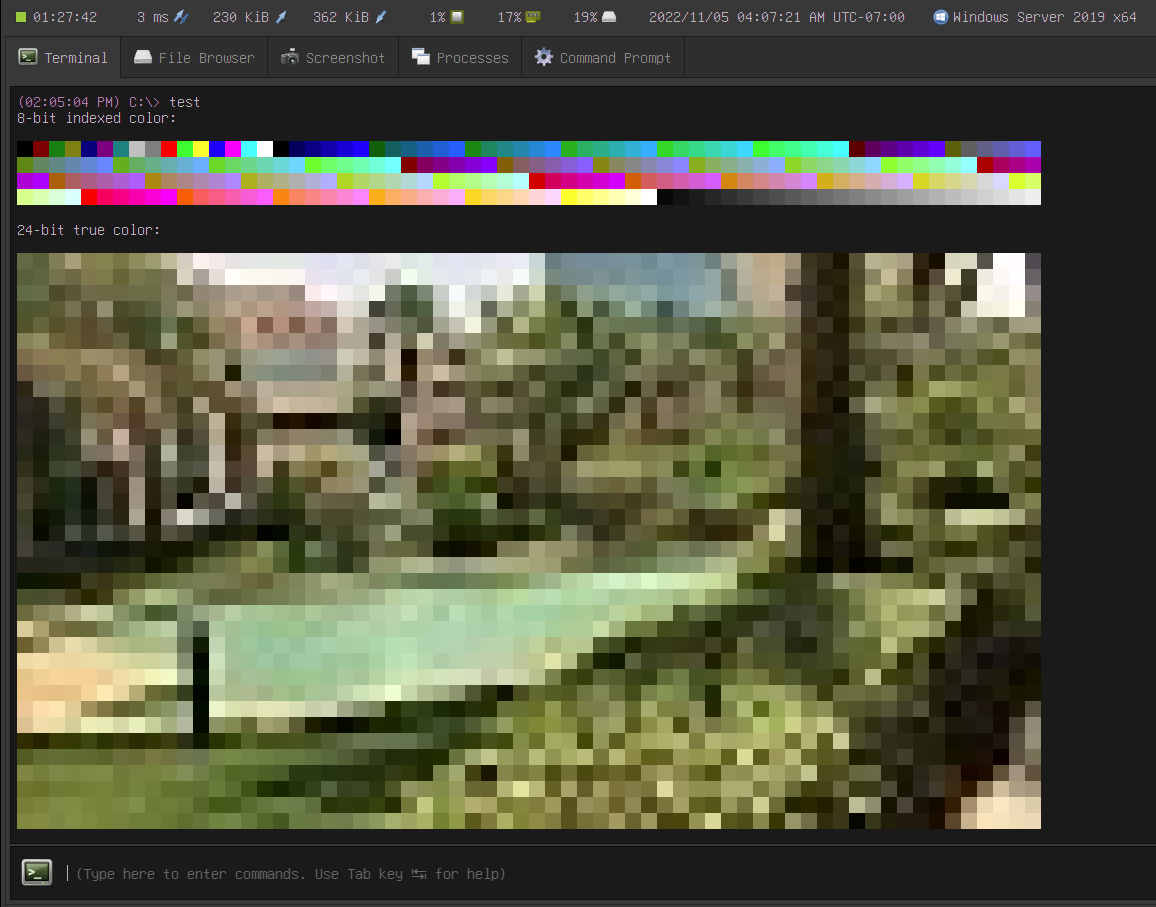
This update adds 8-bit indexed color and 24-bit true color support to the Terminal:
We also added the lls, lpwd, and lcd commands as a convenient way to navigate your own local filesystem:
llsto list local contents of local directorieslpwdto show the current local directorylcdto change the current local directory
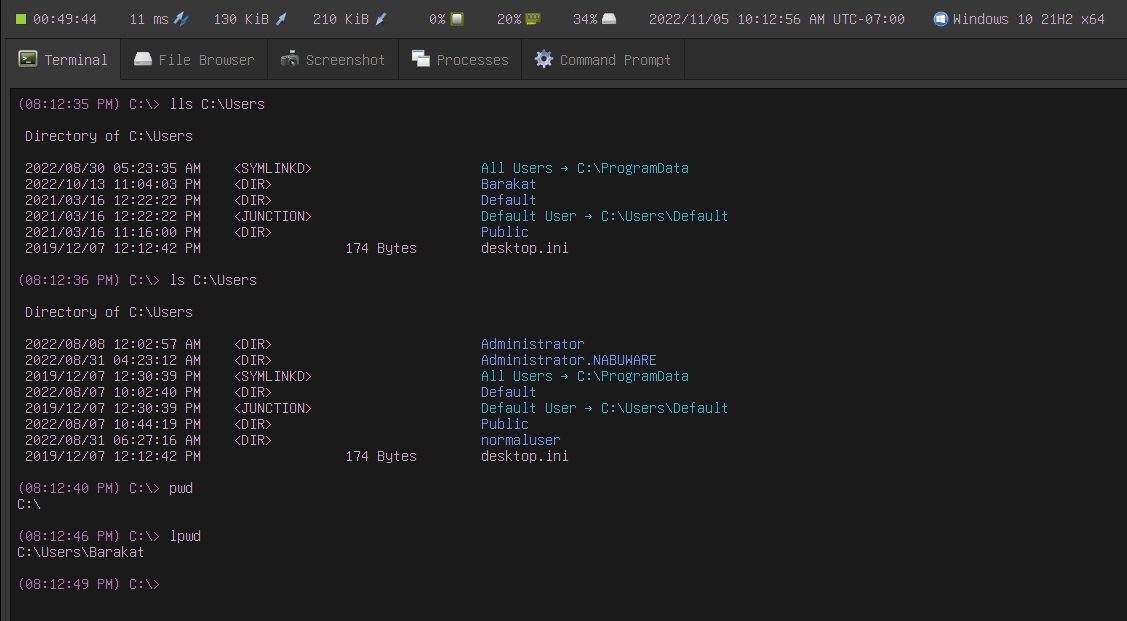
The output of these commands is identical to their remote counterparts: ls, pwd, and cd.
Let's get in touch
Are you looking to purchase Network Exploit, or do you have any questions?