Network Exploit Update 2022.12.1
New lateral movement method
With the release of Windows Vista, Microsoft introduced the new Task Scheduler 2.0. Task Scheduler 2.0 improved over Task Scheduler 1.0, which was part of Windows since the early days of Windows NT. Task Scheduler 2.0 added ‒among many other things‒ the ability to schedule tasks implemented as COM objects called COM handlers as an alternative to regular executables. COM handlers have the extra benefit of allowing suspending and resuming tasks. Almost no Windows developer uses this feature. If somebody wants similar functionality, he will probably go with the well-documented Windows Services.
In this update, we added another lateral movement method that uses this feature by pushing a COM handler that bundles the implant to the target you specify. You must explicitly choose this method by passing the option --method com-handler to lateral-move. Be aware that remote registry and task management must be enabled on the target to use this method; this is usually the case in domain environments. If you are experimenting with it on your VM, enable both.
Self-deleting implants
If you used lateral-move or elevate-integrity, you might notice that they no longer display cleanup instructions. In this update, we added the ability for the implant to self-delete. Once you stop an implant, it will delete itself from the system to ensure no artifacts are left behind after an engagement.
Sometimes you may successfully get the implant to run on some machine. However, it cannot connect to the operation server due to a permanent networking issue. In this case, the implant will try to connect periodically to the operation for 12 hours; then, it will give up and self-destruct.
If the failure occurs after a previous successful connection, it will assume the failure is temporary and will try to reconnect periodically for 72 hours, and then it will self-destruct.
New .NET assembly loader
Having a robust implant is one of our top priorities. We implemented many measures to avoid issues such as memory leaks, dangling handles, process-wide modifications, etc. The implant might co-exist in another critical process, and we want to avoid interfering with it or ‒worst‒ crashing it.
All this goes out of the window once we allow third-party tools to run in the same address space.
This update added a new .NET assembly loader to load your .NET tools in memory without ever touching the filesystem or affecting the implant or its host process. It is fast, reliable, and it-just-works™.
Here is an example of deploying an unmodified Seatbelt (a .NET security tool) on an up-to-date Windows 11:
Terminal environment variables support
Terminal now supports environment variables. We chose CMD syntax for the variables, for example, %WINDIR%. Now you can execute a command such as ls %WINDIR%\System32.
The environment variable expansion is context-aware. For example, a command such as ls %APPDATA% will expand the environment variable of the target, whereas lls %APPDATA% (local ls) will expand the environment variable on your local computer.
Recovering Recycle Bin deleted files
In this update, we added a new tool, recycle-bin. This tool lists the deleted files in the target Recycle Bin and lets you pick and recover files individually. The Recycle Bin may contain personal notes or installation instructions with sensitive information such as credentials.
To list deleted files, run recycle-bin. To download a file of interest, you will see a recovery command in the "Recovery Command" column. Just copy the recovery command and execute it, and Network Exploit will download the file in the background. To see the download progress, go to the Transfers in the File Browser tab or type transfers as you would with regular downloads.
Retrieving PowerShell history and Most Recently Used menu items
This update introduces two new tools, powershell-history to retrieve the history of executed PowerShell commands and run-history to retrieve the items in the run history.
These tools help you find paths, administrative scripts, or previously executed commands containing credentials or information interesting to you.
Creating and editing text files remotely
Rather than editing a text file locally and uploading the file, you can now create plain text files remotely using the mkfile command. You can specify the encoding by passing the -e/--encoding option. It uses UTF-8 by default. To add content, you can pass it directly or use the edit tool for editing using your default text editor.
UI Improvements
Targets in the Network Map order are now consistent with the target tab. The targets and the tabs are ordered from oldest to newest, so you can visually map between the two more quickly.
In addition, you can now increase the Terminal font using the context menu and the keyboard shortcuts: CTRL++, CTRL+-, and CTRL+0 to zoom in, zoom out, and reset the font size, respectively.
put, get, and transfers commands are now integrated with the File Browser. You can, for example, download a file from the Terminal and see the progress in the File Browser, and vice versa.
systeminfo improvements
The systeminfo tool now reports Windows 11 release names such as 21H2 and 22H2.
It now also distinguishes between workgroups and domains more accurately. If the target is joined to a domain, it displays the domain information; otherwise, it shows the workgroup information.
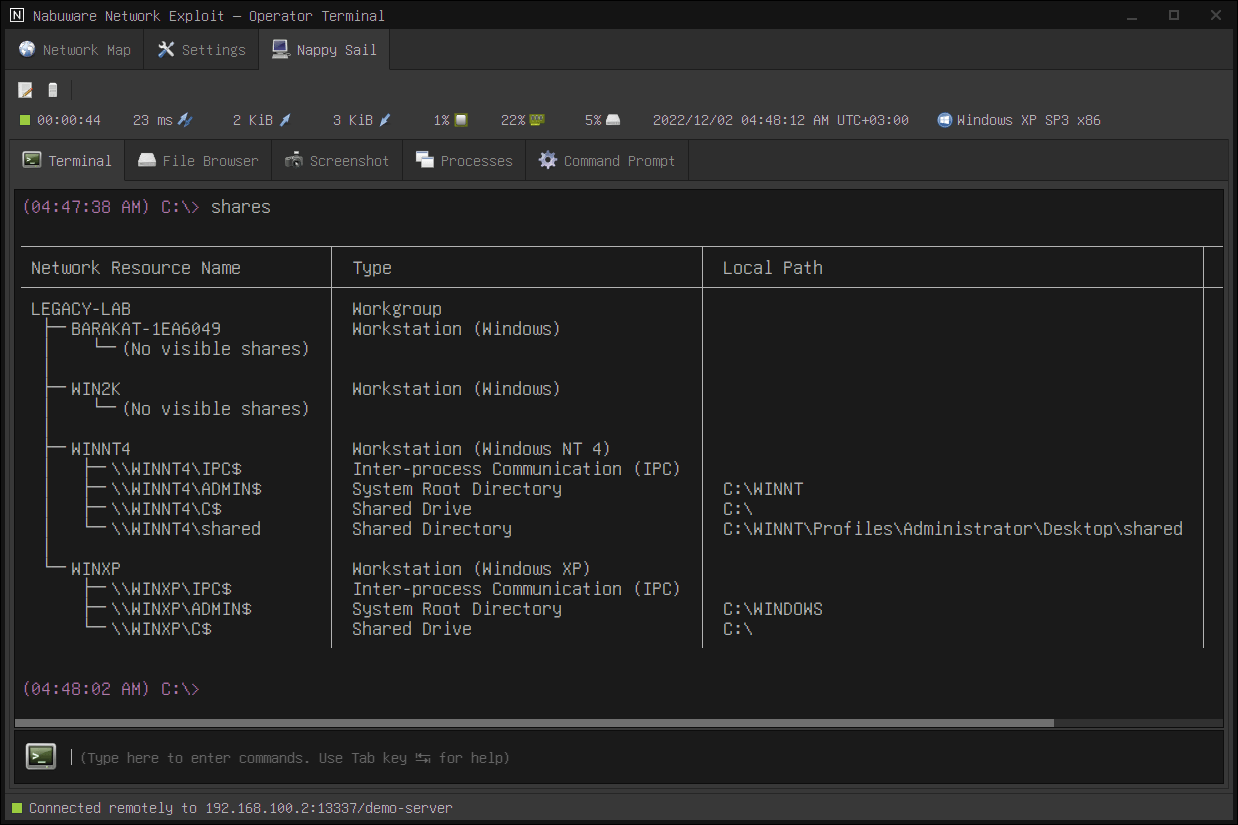
shares improvements
The shares command lists the shared network resources on a given target. If you run the command without specifying a target, it will visually map the nearby workgroups as a tree along with every shared network resource in those workgroups.
Resolved issues
This update addresses some previous issues:
- Child process creation could fail if the process spawning takes too long due to, for example, a very slow disk.
- The
reg-deletetool did not work when trying to delete registry entries on a remote computer. - Tools such as
pson CJK Windows builds, such as those using Chinese, may fail because of an encoding issue. editdid not previously allow editing blank files.
All the previous issues have been resolved with this release.
If you have any questions or want to purchase a Network Exploit, don't hesitate to contact us on the form below.
Let's get in touch
Are you looking to purchase Network Exploit, or do you have any questions?