Network Exploit Update 2022.9.15-EA
We've just released Nabuware Network Exploit 2022.9.15-EA, an early access update. This update improves various communication subsystems to improve concurrency and to make the overall system more responsive. This update includes parts of the upcoming features in the update 2022.10:
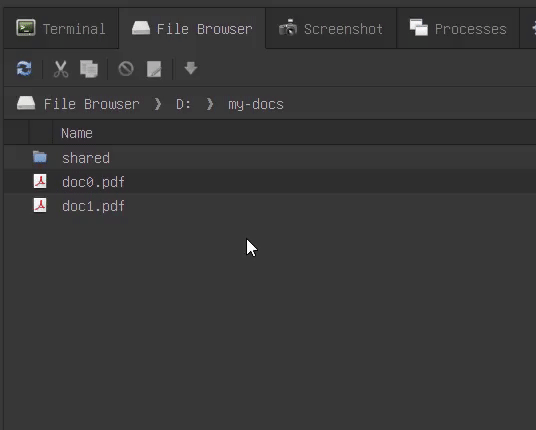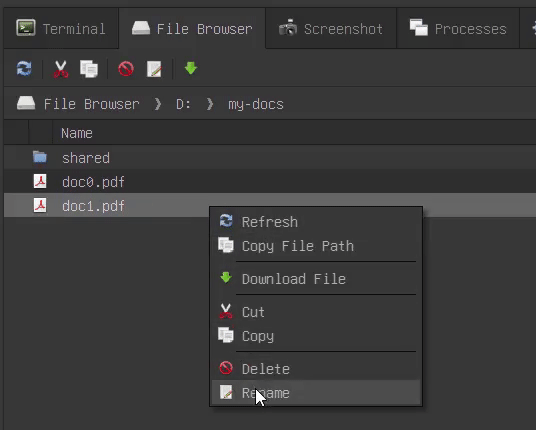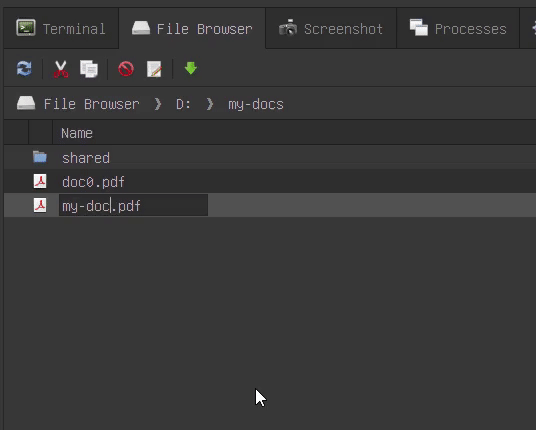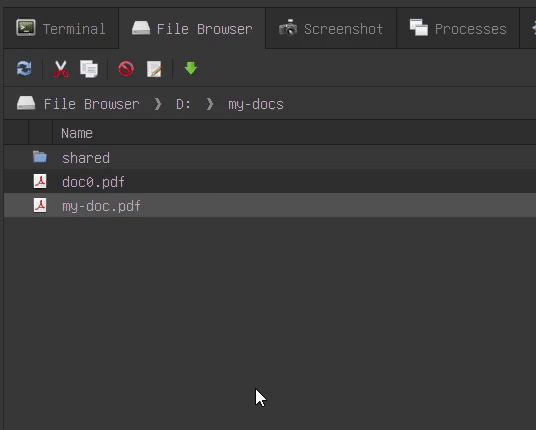
Now, you can rename files in place rather than using a rename dialog box. All expected behaviors, such as reverting to the original file name, work as expected.
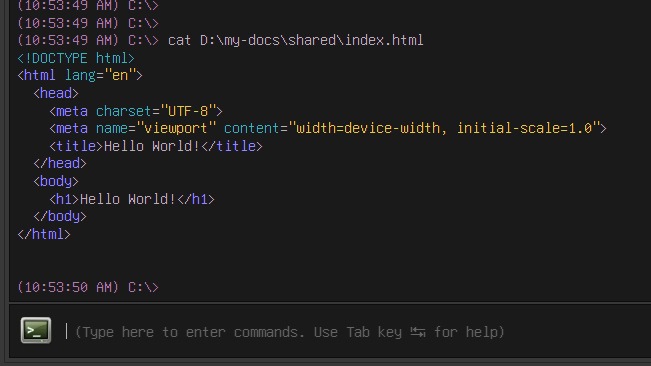
The cat command automatically recognizes common plain text file formats, and syntax highlights their contents. It already recognizes binaries and hex dumps their contents.
We fixed a race condition in the UI that causes Network Map to malfunction when it receives updates before rendering finishes. We also fixed a bug that caused the Terminal to stop when trying to interact with a computer that lost connectivity while the UI was closed.
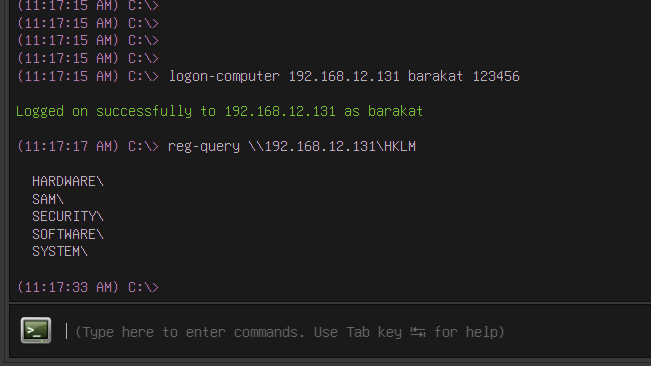
We introduced a new tool, logon-computer, as an alternative method to logon-user to authenticate against remote services.
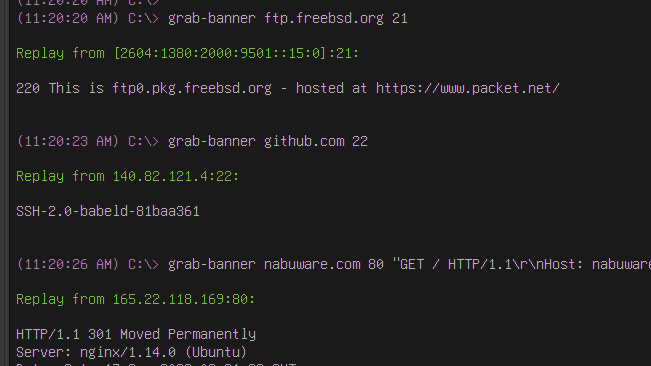
As a complement to the port-scan tool, we also added a dedicated grab-banner tool to connect and grab the banner of network services such as SSH, FTP, and HTTP. It supports both UDP and TCP.
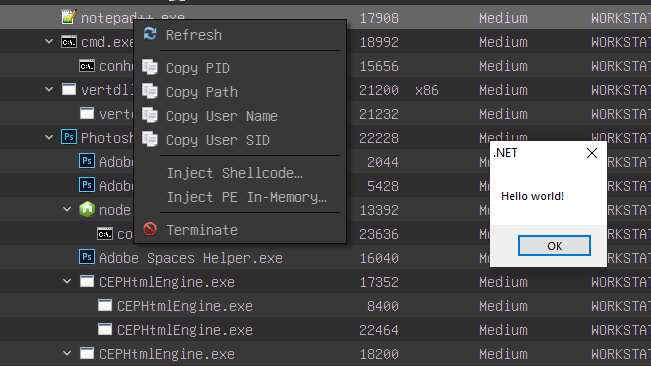
The DLL injection functionality now prevents injecting DLLs with an incorrect processor architecture. It now also detects injecting .NET assemblies and switches strategy transparently. We renamed this functionality to "Inject PE In Memory" to reflect this change.
Let's get in touch
Are you looking to purchase Network Exploit, or do you have any questions?