Network Exploit Update 2022.10.1
We've just released Nabuware Network Exploit 2022.10.1. In this update, we added new tools, extended the capabilities of existing tools, and made various improvements to Network Exploit.
To simplify working with tools such as lateral-move, you can now refer to listeners using human-friendly names such as "tcp-8080" instead of internal machine IDs—which are no longer accessible. And, of course, you can change these names as you see fit.
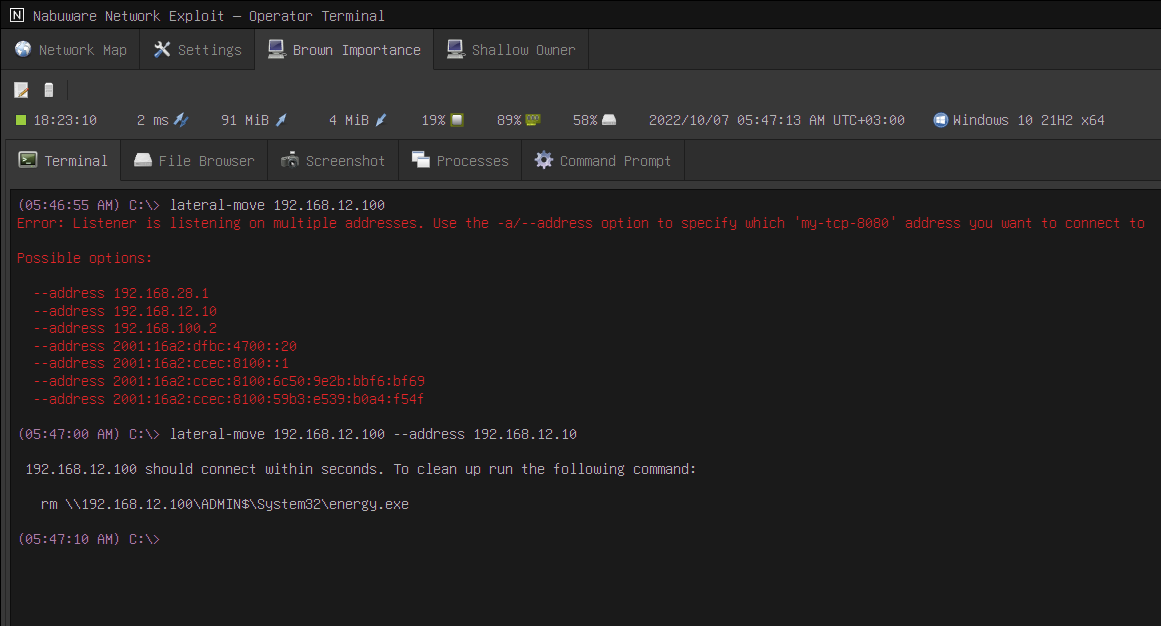
lateral-move —a tool for propagation and lateral movement across the network— now infers all its settings. It detects the target operating system and architecture. It falls back to the current target listener if you don't supply one. If it cannot decide, it gives you a suggestion.
Previously in 2022.19.15-EA, we introduced the tool logon-computer. We changed its name in the final release to connect-computer and added its counterpart, disconnect-computer.
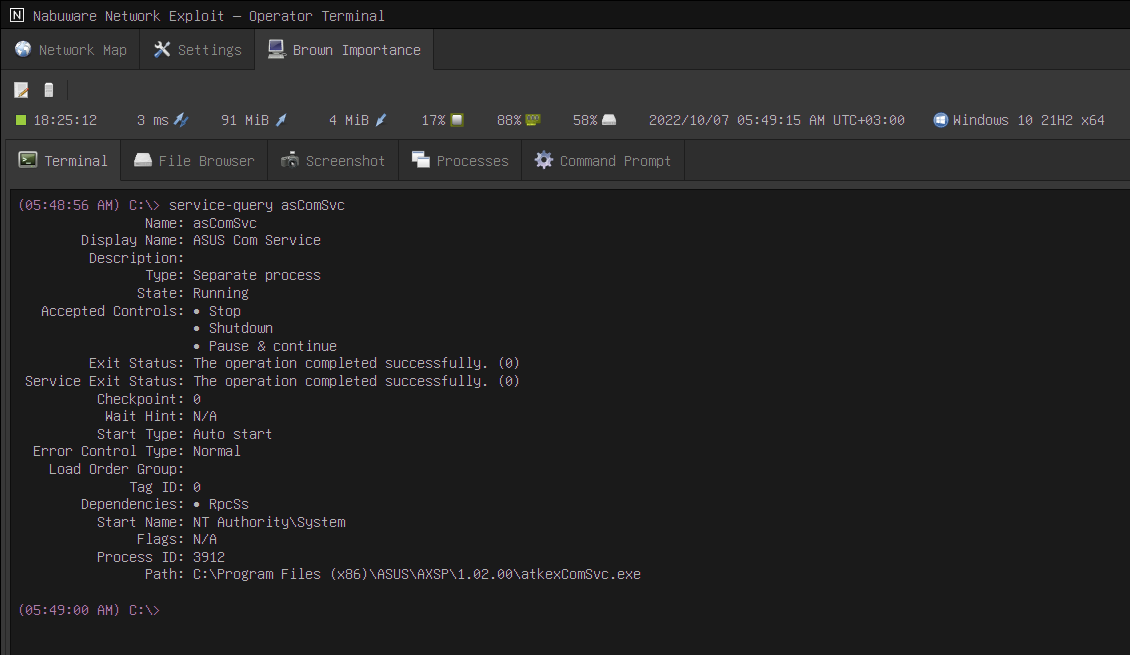
In this update, we added a new set of tools that give you complete control over Windows NT Services. These tools are:
service-queryto query and list servicesservice-editto modify and create servicesservice-controlto start, stop and control servicesservice-deleteto delete servicesservice-permissionsto display service permissions
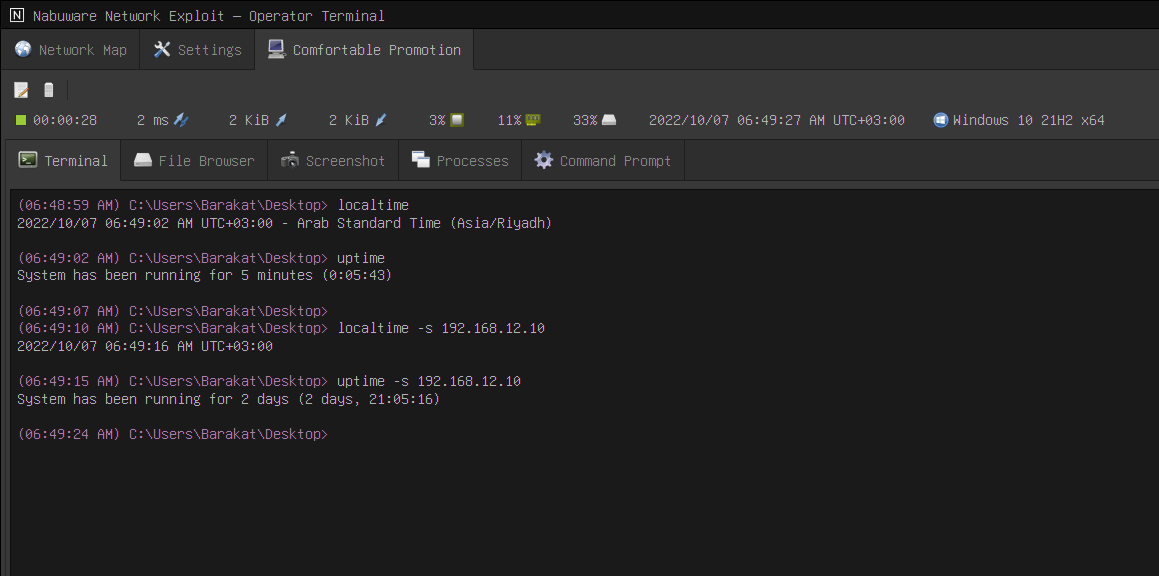
The localtime and uptime tools can now display another computer's local time and uptime without having to deploy and implant on that computer. It is valuable for making persistence-related decisions and launching attacks that require precise timing.
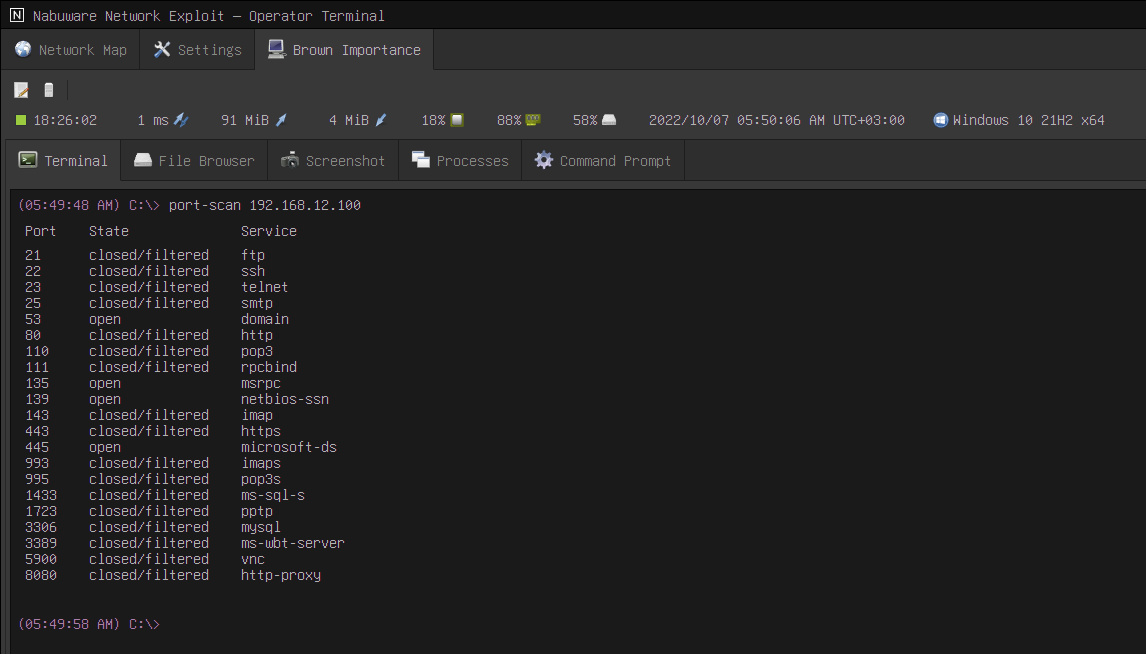
The port-scan tool no longer requires a port to start the scan. It will scan the most common 20 ports if you just supplied a target.
This update includes all features of the early access update, 2022.19.15-EA.
Let's get in touch
Are you looking to purchase Network Exploit, or do you have any questions?