
Network Exploit
For Red Teaming Assessments and Threat Actor Simulation
Network Exploit provides your cyber security team with the tools to assess your organization's security from the perspective of threat actors and an extensible framework for building new tools and modeling new threats.
Benefits
Network Exploit helps you proactively identify unseen risks and improve security controls by anticipating threat actors' actions, testing incident response plans, and conducting red teaming assessments in a cost-effective and efficient manner.

Identify and treat risks proactively
Network Exploit helps you proactively identify unseen risks that may arise in your organization and take proactive steps to treat them, preventing them from becoming significant problems in the future.

Create better security controls
With Network Exploit, you can create better security controls and improve existing ones by anticipating how threat actors would operate in your organization's threat environment.

Improve incident response plans
Network Exploit helps you test the effectiveness of your incident response plans by exercising responding to simulated incidents. You can accelerate the feedback cycle to improve your preparedness in real incidents.

More red teaming assessments
Third-party red teaming assessment exercises may be expensive, time-consuming, and broad in scope. With Network Exploit, you can conduct red teaming assessments anytime, by anyone on your team, and as narrow as you need to.
What is red teaming ?
Red teaming is a methodology used to identify potential threats by simulating and anticipating the actions of an adversary.
The goal is to challenge assumptions and test the effectiveness of security controls and plans by examining them from the perspective of a potential attacker.
The term "red teaming" originated in the Cold War era, when it was used by the US to anticipate the actions of the USSR, who were referred to as the "red team." Today, red teaming is used to refer to any simulated adversarial activity.
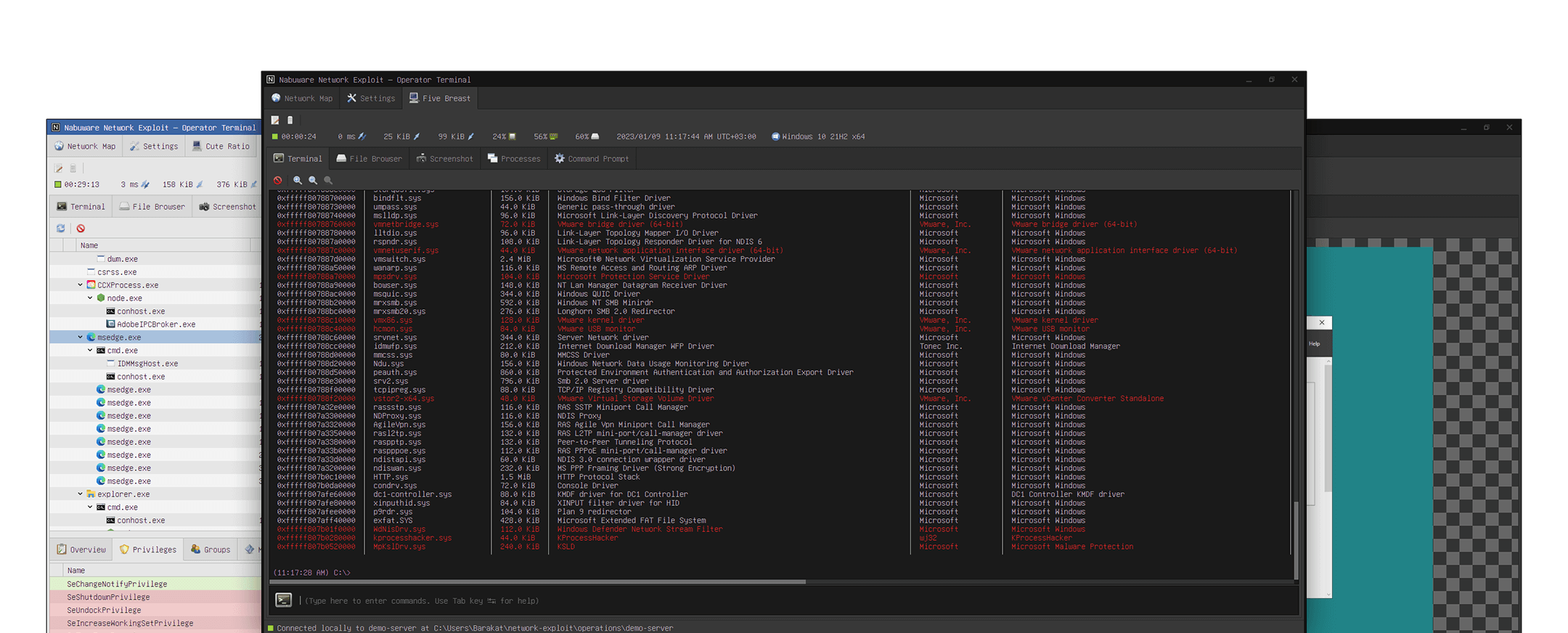
Features
Network Exploit is a comprehensive red teaming solution that simulates various types of threat actors and allows for the simulation of all stages of the cyber attack lifecycle with robust features, ease of use and no complex setup.

Threat actor simulation
An extensive builtin set of red teaming tools to simulate all types of threat actors

Attack lifecycle simulation
Simulate all stages of the cyber attack lifecycle, such as reconnaissance, lateral movement, and exfiltration

Powerful networking
Robust peer-to-peer networking capabilities to stress test your network security controls

Seamless remote access
Seamlessly operate on remote computers as if you were working locally

Extensible framework
Powerful extensibility framework for building new tools using Python

Windows support
First-class Windows support. Supports legacy targets as old as Windows 2000

Easy to use
Friendly, easy-to-use user interfaces, both graphical and command line

Quick install
No complex setup or infrastructure is required. Ready to use in less than 30 seconds

A lot more
Network Exploit packs many features that make it one of the best in the market
Showcase
This is a collection of videos to showcase key features of Network Exploit and its powerful functionality and versatility. These videos will give you a glimpse into what it can do.
Lateral movement and peer-to-peer networking
Built-in host and network reconnaissance tools
Browsing filesystem, enumerating processes and taking screenshots
Scripting and debugging support
Compare plans and pricing
Enterprise
7734 USD / per year
VAT included
✓ One-year user subscription
✓ All features included
✓ Unlimited usage
✓ Monthly updates
✓ Online technical support
Custom
Variable pricing
VAT included
✓ One-year user subscription
✓ All features included
✓ Unlimited usage
✓ Monthly updates
✓ Custom support
Let's get in touch
Are you looking to purchase Network Exploit, or do you have any questions?


